(en) wildcard certificate
Yesterday, another email came in from Let’s Encrypt Expiry Bot, warning me that the certificate to one of my subdomains are going to expire and I should renew it soon. I have a lot of subdomains going on in here, and I requested certificates for each of them on separate timings so this email come rather often. I hear it’s going to be discontinued soon, though…
But the point is, I have a lot of subdomains going on and each have their own certificates. This is because I use the command certbot --nginx to request for these certificates. Certbot reads my nginx configurations and see that I have a lot of server blocks defined, every single one having a different server_name. Following that, Certbot requests a certificate for each server block separately because it’s how it’s programmed to do.
But since they’re all part of the same domain anyway, wouldn’t it better to just request one certificate that works for the entire domain? Yes. But is it possible? Turns out, yes.
Interlude. Do you even need certificates in the first place? you might ask me. There’s only static HTML around here. There’s nothing here that needs encrypted! you might also interject. True, but did you know that .dev domain can only be accessed via HTTPS? That’s right, so we’ll all get hit with an invalid certificate warning if I don’t request a certificate for this domain. But even if it isn’t so, I’d still get a certificate for this domain anyway because it’s good practice. The web is and should be going for a secure-by-default model, and with the certificates being free and easy to get, I don’t see why not.
Back on topic. A little Googling tells me I shouldn’t rely on Certbot’s nginx option to scan my server configurations. I should manually request for one set of certificate that works for my domain and all subdomains for it via wildcard.
There’s a little catch, though. Unlike subdomain-specific certificates, to get a wildcard certificate I need to prove that I own the whole thing. This is by doing a DNS challenge; I have to put some TXT record to my domain’s DNS config and prove that I have control over the domain. But since I’m using Cloudflare, I can get this part automated for me too, using Certbot’s Cloudflare plugin.
So I installed the plugin, fed it my Cloudflare API keys, and ran this here command:
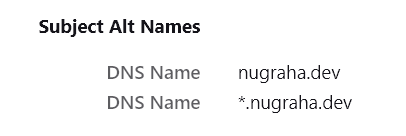
sudo certbot certonly --dns-cloudflare -d "*.domain.dev" -d "domain.dev"
A little bam here and there, and now I get a certificate that works for my entire domain. Check it out by clicking on the lock icon on your browser and viewing the certificates. One downside is that since Certbot doesn’t read my nginx configurations, it also doesn’t write to it and I had to manually specify the certificates on my nginx config files. It doesn’t take a minute though, so I guess it’s not a downside at all.